Kibana MCP
2025-04-06
I used a combination of Cursor, Gemini 2.5, and Claude Desktop to create a simple FastMCP server that would give an appropriately configured MCP client the ability to take some simple actions in Kibana.
The most time consuming element of this in the end was having an appropriate test environment that could be spun up with a single command. I needed a Kibana/Elasticsearch instance where the Kibana system account could authenticate with Elasticsearch, and Elasticsearch was pre-populated with some data, a detection rule, and as a result an alert. Cursor really proved its worth here by managing to get into a beautiful feedback loop where it would run the initialising bash script, inspect the logs from Kibana STDOUT to evaluate if everything had gone as planned, tear down, and start again until the errors had been resolved. Repeatedly tearing down and spinning up big Java docker containers did make my laptop a little hot.
I was hoping to use Cursor as my MCP client, however the current means by which server and client talk is STDIO. Cursor doesn’t capture this, and provides some very opaque debug messages when the server fails to start. This was so frustrating that I tried to use Claude Desktop instead. Claude writes errors from STDIO to a specific logfile for the purpose of this kind of debugging which was super helpful.
Wishlist going forwards:
- Tools for detections engineering: Exception editing, detection editing
- Case management: Create cases for suspicious alerts for human analyst to review
- Expand test env. More detections, more dummy data
https://github.com/ggilligan12/kibana-mcp
RAGeQUIT
2024-08-13
In June 2024 I took a 1-week course in malware. Apart from a brief play with Radare with a Ghidra plugin to have a rummage around the WannaCry malware this course was mostly non-technical, with a heavy emphasis on the economics and strategy of what it takes to run a malware campaign. This was my introduction to what it means for disruptors and law enforcement to ‘impose cost’. A campaign cannot be defeated until the economics are understood. The campaigns stop when it is no longer profitable to run them.
The assignment was to plan a campaign, and a strategy to mitigate that very same campaign. I conceived RAGeQUIT, a Chrome extension that deploys a crytominer. The campaign to spread the extension leans hard into LLMs, and the payload it deploys takes inspiration from ALPHV/BlackCat and WARMCOOKIE to establish persistence and evade defences. Link below.
https://gilly.tech/assets/ox_mal.pdf
The Rust Move Semantic
2024-06-18
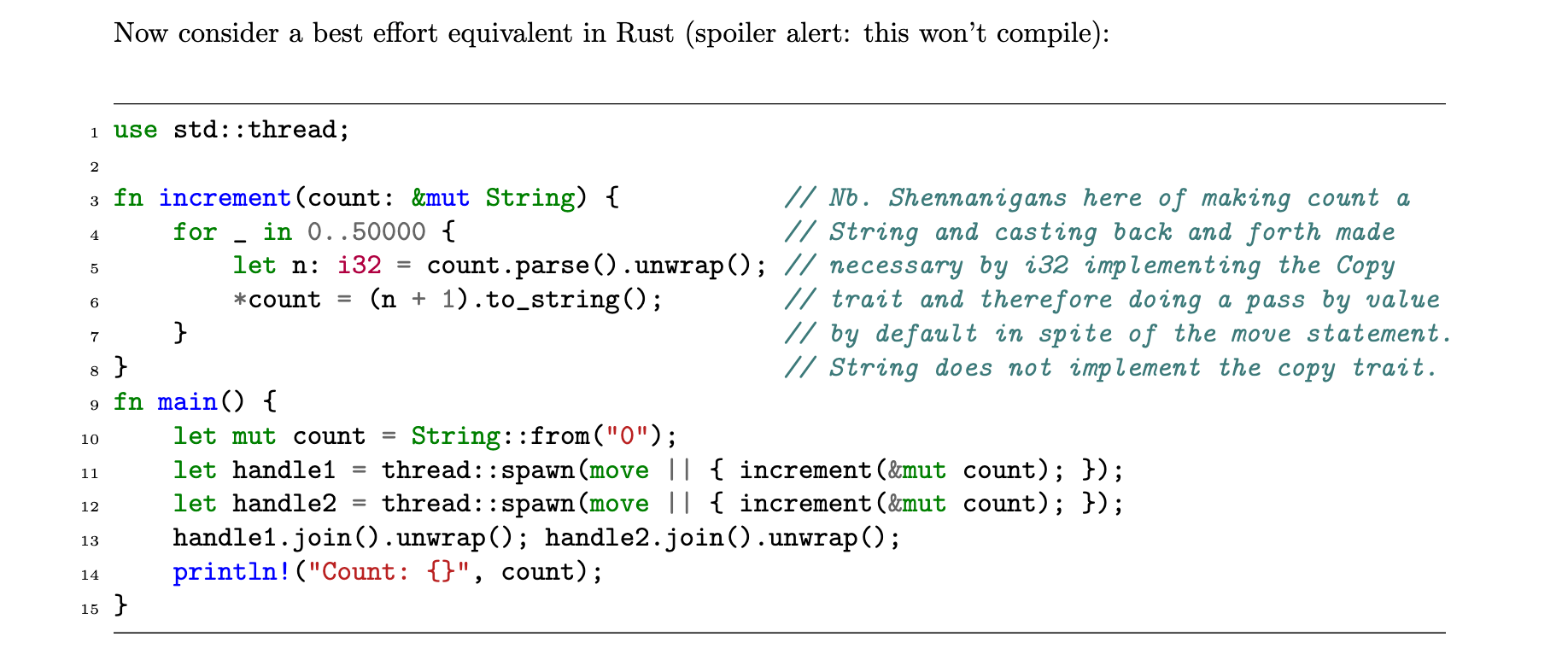
The Rust hype-train must now count among the longest running in modern software engineering. Thanks to the fantastic David Aspinall my assignment for a Secure Programming course as part of my MSc gave me the opportunity to get familiar with Rust’s Move semantic, how it mitigates race conditions, UAF and Double Free vulnerabilities, and the extent to which Rust truly embodies Correctness by Construction.
https://gilly.tech/assets/ox_scp.pdf
We Make Boxes Crisis & Incident Management
2024-03-26
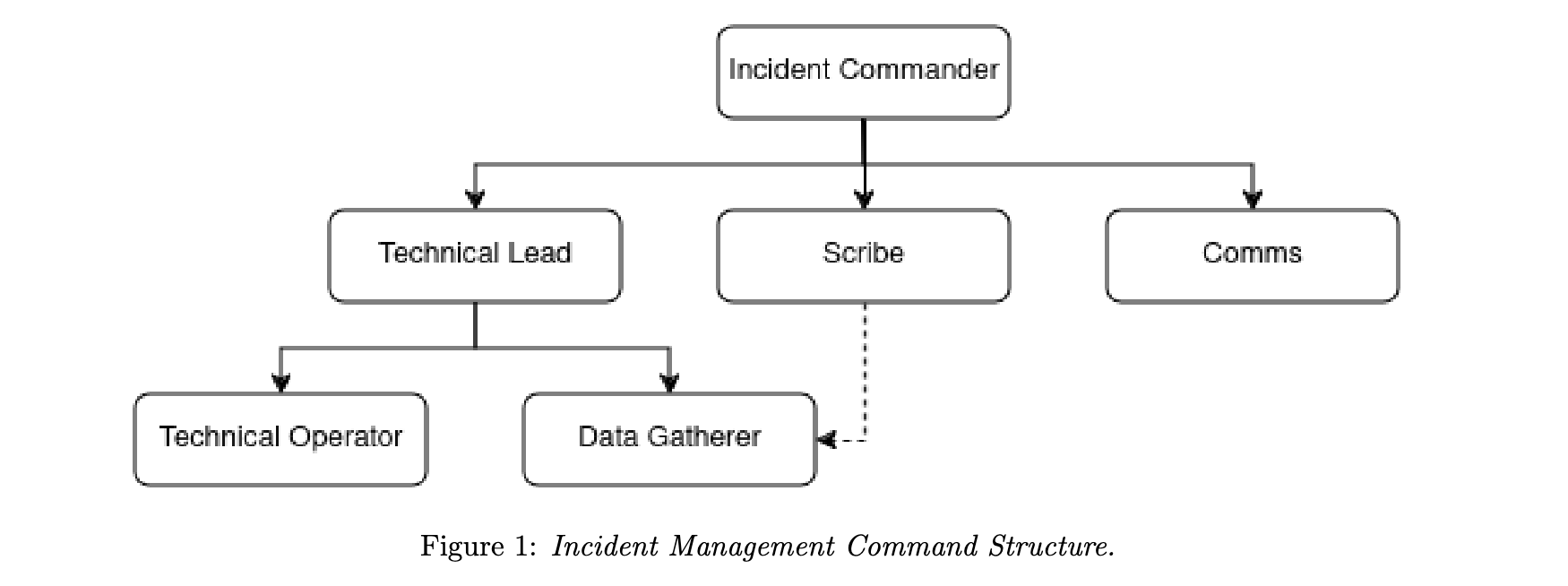
2 months ago I was tasked by David King with coming up with an Incident and Crisis Management procedure for a fictional Box Manufacturing company. The link below was the result. This was an interesting exercise in trying not to write shelfware, ie. a document whose only function is to say to an auditor that it exists, and is never read by anyone.
This provided a good opportunity to think about the importance of regular incident simulation, the distinction between incident and crisis, and how to plan for disaster without being overly prescriptive.
https://gilly.tech/assets/ox_sim_design.pdf
HTTP/2 to HTTP/1 Conversion Anomalies
2023-12-05
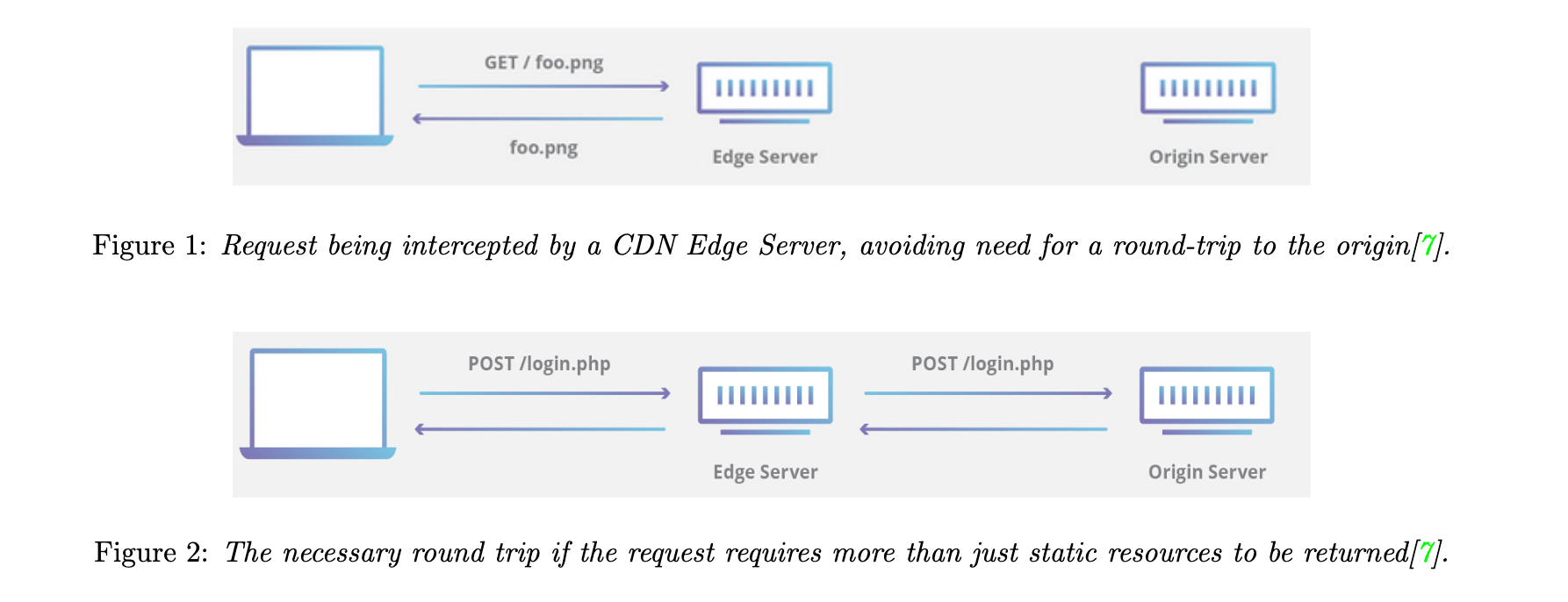
In October 2024 I took the first course of my part-time MSc: Network Security. The course was led by the lovely Andrew Paverd, who gave us a fast-paced but shallow overview of security issues to be found at all levels of the OSI stack. The course was enjoyable, with an assignment that entailed a deep review of security issues in WPA2 and HTTP/2 to HTTP/1 conversion anomalies as laid out in this USENIX paper: https://www.usenix.org/system/files/sec22-jabiyev.pdf. The amount of study required to adequately complete the assignment made for a great learning opportunity. Enjoyed this a great deal. Assignment linked below:
https://gilly.tech/assets/ox_nes.pdf
based.cooking
2021-07-28
Found my new favourite website. Some guy named Luke has become very angry at what he calls ‘soydevs’ and their recipe pages filled with trackers, ads, unwanted content, comment sections, bloat, login portals, popups, and megabytes upon megabytes of Javascript. As a result he set up a static site with very little styling, to open source the problem of collating online recipes. Contributions are made by GitHub pull requests. Love it. Will be contributing a chickpea curry soon. based.cooking
Site finished! Almost...

2020-06-07
I mean I still need to include a showcase of my undergraduate uni work and pay tribute to CTF somewhere in here… but hey no more template rubbish lying around!
pi.py
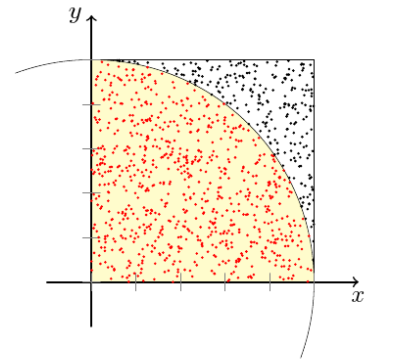
2020-06-02
My concern with attempting to keep something resembling a blog is that it will inevitably die due to neglect. The obvious solution is to have something simple that obliges me to make some small regular contribution, no less often than once a month. I’m going with programatically calculating . Once a month, always in a different way, always with a different language. This will start fairly trivially, though I envision it getting fun.
I’ll begin with Python, and one of the most intuitive methods of calculating : a basic monte-carlo estimate. The intuition is illustrated with the graphic above, draw a quarter circle of radius 1 inside a square of side length 1. Then start dropping points at random inside the square. The probability of a point falling inside the quarter circle is . Therefore if we drop a large number of points , we would expect points to fall within the circle, and to fall beyond it.
Given a point with coordinates on the unit square:
Therefore if we choose a large enough :
giving us an expression for of:
Thanks to some nice vectorisation from numpy this can be written very succinctly:
from numpy import floor as f, random as r
n = 2**27
print(4-4*sum(f(r.random(n)**2+r.random(n)**2))/n)
This little block runs in 10 seconds or so on my laptop and consistently gives accurate to three decimal places. Not too shabby for the most simplistic method available.
Adversarial Security Models

2020-05-06
If my study of quantum cryptography has taught me anything, it’s that our threat modelling can never be too extreme.
404 Post
2020-05-02
For a time in ancient Athenian society the city was presided over by a figure called the Archon. The Archon would be democratically appointed, to hold the post for a year. Sometimes they were also known as the Eponymous Archon, since their names could be used to date the years, eg. 682, Creon.
After suffering defeat at the hand of oligarchic Sparta in the Peloponnesian War in the 5th century BCE, Athens was subjected to the rule of an oligarchy. A handful of men backed by Sparta, who came to be known as the Thirty Tyrants, took charge. The rule of the Tyrants was brutal, and brief. After less than a year in power they were deposed in a rebellion led by the exile Thrasybulus, and democracy was restored.
Later historians refer to the year 404 BCE, the year Athens was subdued and without a legitimate democratically appointed Archon, as “the Anarchy”. So given the chance to query them: “Who was the Archon in the year of the Thirty Tyrants?”, they could conceivably have replied:
“404, Archon not found”
This is a coincidence, but it brings a smile to my face to think of it as a great easter egg of the internet. Enough so that a duplicate of this post serves as the actual 404 page of this website.